What does Corrected Cloud look for?
Understanding what problems Corrected Cloud can spot
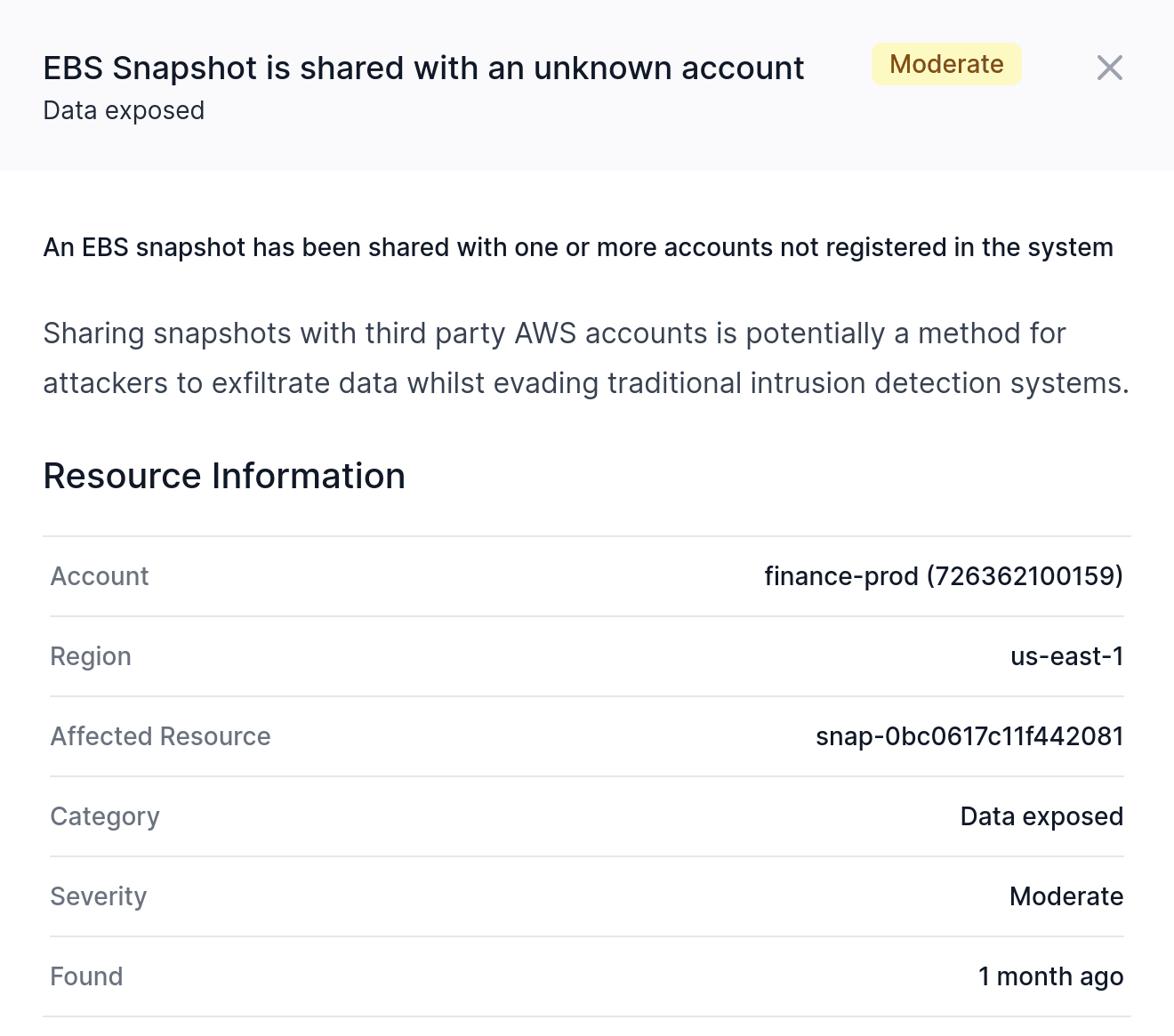
Data Exposed
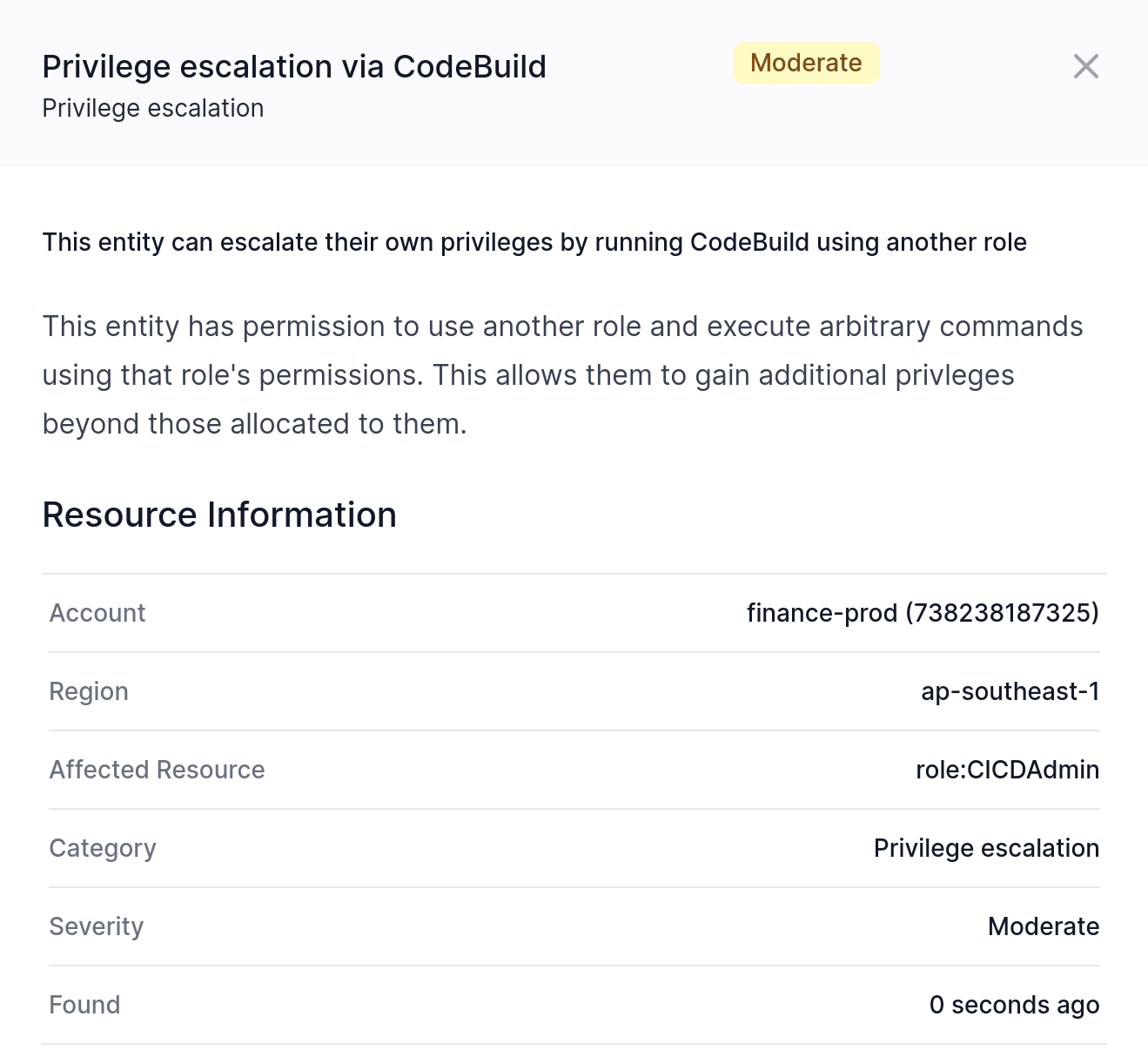
Privilege Escalation
An IAM user or role with the wrong set of permissions can utilize those permissions to gain additional access beyond that intended. Because Corrected Cloud features a full IAM policy evaluation engine it is possible to find such vulnerabilities within seconds of their creation, even when they require complex operations to exploit.
In the most simple form, privilege escalation would be possible when a user or role can directly alter their own permissions, either by editing policies attached to their resource, or by attaching new additional permissions.
Corrected Cloud is also able to detect more complex privilege escalation vectors, for example an IAM user or role that can create a new Lambda function using a role which has permissions to then modify the original user or role. Corrected Cloud takes into account permissions boundaries when evaluating escalation paths.
Credential age too high
Unrotated credentials present a security risk on the basis that the longer they have existed, the greater the potential risk of them having leaked.
As always with Corrected Cloud the context of the credential is evaluated as part of the finding. For example, we do not raise findings for passwords which have not been changed in a long time if multi-factor authentication is also required to log in.
Excessive Permissions
Minimizing the permissions for every resource is a key part of effective security. Unfortunately, it can be difficult to determine exactly what permissions are required, and it’s all to easy under time pressures to simply provide wildcard permissions to get things working and then move on.
Corrected Cloud will find and alert on situations where these excessive permissions exist. For example, we provide notifications for EC2 instances that can delete databases and their backups, and Lambda functions that can alter S3 bucket policies to make the contents public. Because Corrected Cloud features a full IAM policy evaluation engine, it understands the effective permissions of every resource in your environment, ensuring alerts are provided regardless of how a permission set is arrived at.

Remote code execution
Remote code execution vulnerabilities are some of the most dangerous mis-configurations available.
This category covers both direct remote code execution (for example, the ability for an attacker to update Lambda function code and invoke) and indirect execution, for example by altering a Docker image you are directly using in an ECS task.
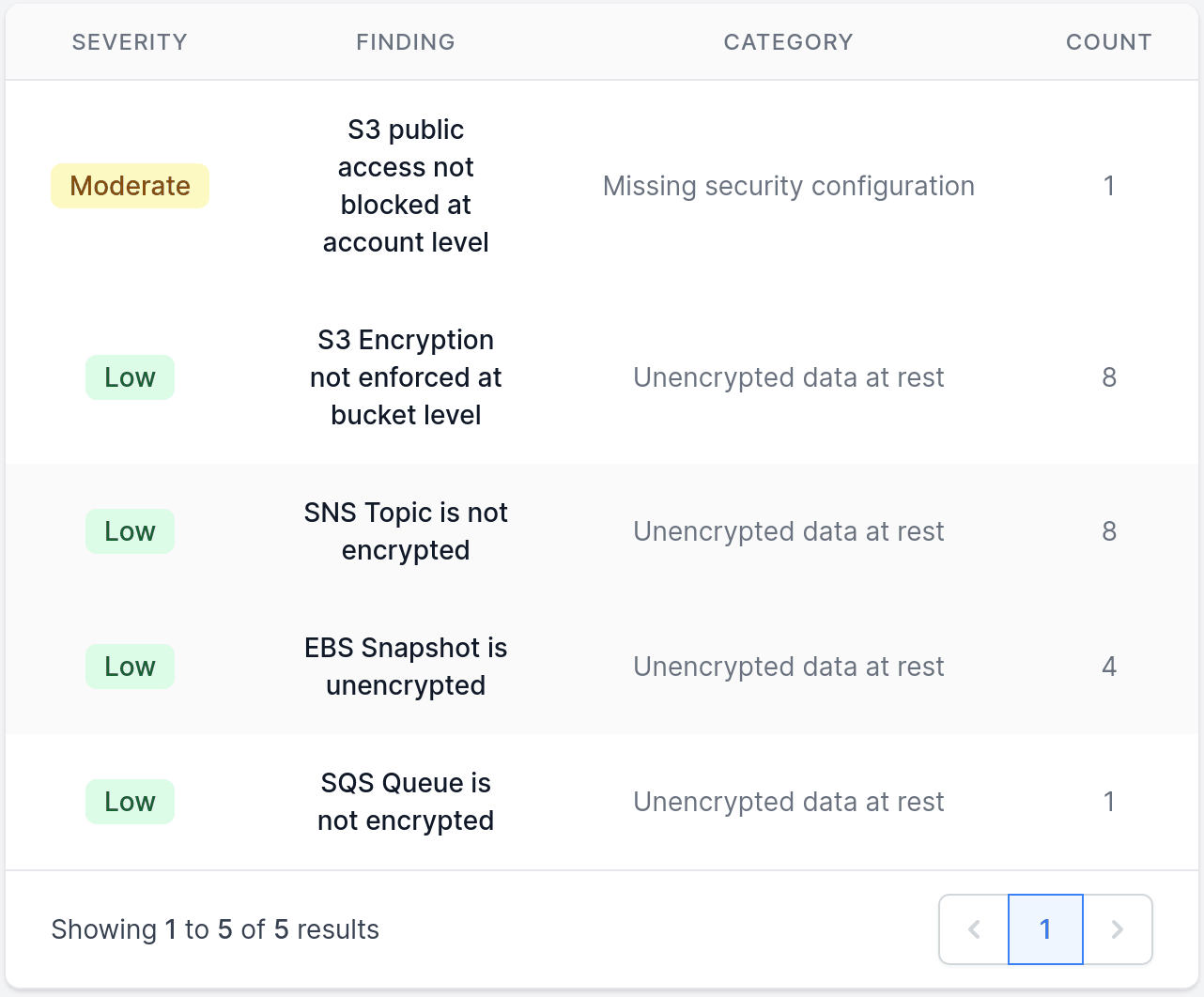
Missing security configuration
AWS offers a number of services to detect security breaches in your environment. Whilst Corrected Cloud focuses on preventative controls, services such as AWS GuardDuty find suspcious activity that has occurred in your account.
This category provides warnings when relevant services are not enabled. As always, we strive to only provide relevant warnings, so for example you won’t be warned that you do not have Elastic Container Repository (ECR) image scanning enabled if you are not using ECR anyway.

Deprecated configuration
Technology provides a constantly evolving market, and security is no different. Warnings in this category are for configurations which used to be acceptable, but now have better alternatives.
An example of the type of warning provided here would be load balancers that still allow TLS 1.0 encryption, which has known vulnerabilities.
Exposed network
An instance or endpoint which allows unrestricted access to unprotected or minimally protected network ports would be categorized here.
As always, Corrected Cloud uses contextual alerting, so an instance with Redis (a database typically configured without authentication) open to the world and a public IP address would be a highest possible level (Critical) alert. An instance with the same security group attached but no public internet access would be a lower priority alert.
This is in marked contrast to other security tools, which would simply raise an alert based on the security group, regardless of what is was attached to.

Unencrypted data at rest
Data that is stored unencrypted is flagged here.
Most findings in this category are of low severity. This is because although it’s a good idea to encrypt data a rest, not doing so does not necessarily present an immediate security threat.
When making judgements on relative priorities, we look at how easy a vulnerability would be to exploit. To get access to unencrypted data at rest an attacker would need to gain access to the physical storage you are using - something that implies a large failure in the agreed procedures and security posture AWS provide.
Encrypting using KMS is useful because it provides a secondary requirement to get access to the data, enabling more advanced checks on data access.
Unencrypted data in transit
Data that is sent over the network unencrypted belongs to this category.
Findings in this category are typically high priority that data at rest. There are more avenues to exploit this scenario, particularly if this data is sent outside of AWS. Even within the current VPC, functionality such as VPC traffic mirroring can allow the compromise of unencrypted data.